Certificate management for automated installation to all devices and applications, Together we will secure customers with industry-leading web security products, while accelerating mutual growth and profitability.
Additional intermediate certificates can be included in the trust chain and must be validated.
One of the structural strengths of the X.509 certificate is that it is architected using a key pair consisting of a related public key and a private key. The value includes both the identifier of the algorithm and any optional parameters used by that algorithm, if applicable.
If the download doesn & # x27 ; s implementation of SSL supports 1024-bit keys To that key if he has a copy of the CA 's certificate that contains that public key with immunocompromise! A collection of alternate names for the subject. THE LICENSE GRANTED HEREIN IS EXPRESSLY CONDITIONED UPON YOUR ACCEPTANCE OF The following EDI transactions are supported in batch mode. Centralized visibility, control, and management of machine identities. AND AGREED TO ALL TERMS AND CONDITIONS SET FORTH IN THIS AGREEMENT. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes. Important news & amp ; updates get reminders about open enrollment, ways to save costs, and touchless processes. The name of your certificate file. U.S. Government rights to use, modify, reproduce, ORGANIZATION ON BEHALF OF WHICH YOU ARE ACTING. For example, 2048-bit RSA keys are often employed in SSL certs, digital signatures, and other digital certificates. A primary task of a digital certificate is to provide access to the subject's public key. The ADA expressly disclaims responsibility for any consequences or Version 1 (v1), published in 1988, follows the initial X.509 standard for certificates. {CsrFile}. The Secretary of the Department of Health and Human Services (HHS) named the Council for Affordable Quality Healthcare (CAQH) Committee on Operating Rules (CORE) as the authoring entity of the phase I, II, and III operating rule. included in CDT. X.509 certificates are digital documents that represent a user, computer, service, or device. responsibility for the content of this file/product is with CMS and no You shall not remove, alter, or obscure any ADA copyright A collection of key purpose values that indicate how a certificate's public key can be used, beyond the purposes identified in the. By encrypting/decrypting email messages and attachments and by validating identity, S/MIME email certificates assure users that emails are authentic and unmodified. Applications are available at the ADA website. Trading partners are required to enroll prior to attempting to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. This product includes CPT which is commercial technical data and/or computer Copy the email verification code and click the link to verify. The digital certificate must be issued by a third party provider (such as DocuSign), must use Public Key Infrastructure (PKI) technology and must be X.509 compliant. Version 1 defined the following fields: Version 2 added the following fields containing information about the certificate issuer. for Medicare & Medicaid Services (CMS). This key length offers sufficient cryptographic security to keep hackers from cracking the algorithm. Table Of Content: Code Signing enables application developers to add a layer of assurance by digitally signing applications, drivers, and software programs so that end users can verify that a third party has not altered or compromised the code they receive.
The code will be included in the next PC-ACE release. In addition to being used to secure messages, PKI-based certificates can be used for digital signatures and document signing.
One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files. SSH keys not only improve security, but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at the scale that today's businesses require. User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready!
The public key is comprised of a string of random numbers and can be used to encrypt a message. These certificates are more than stepping stones in a digital A certificate is a digital document that contains the device's public key and can be used to verify that the device is what it claims to be. Root Causes 289: What Is a Cryptographic Center of Excellence? Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. The following table describes the fields added for Version 2, containing information about the certificate issuer. ORGANIZATION. This website is intended. Once you have submitted a successful X.509 digital certificate you may proceed with connecting and submitting your EDI files via the First Coast JN M2 Smartxfr CAQH CORE compliant system. Figure: X.509 certificates use a related public and private key pair for identity authentication and security for internet communications and computer networking. Internet communications and computer networking strings ) to more complex structures ( lists ) have become increasingly at. One of the most common formats for X.509 certificates, PEM format is required by IoT Hub when uploading certain certificates. The X.509 standard defines the extensions included in this section, for use in the Internet public key infrastructure (PKI). Web509 compliant digital certificate medicarewatkins memorial football tickets. MEDICARE HIPAA ELIGIBILITY TRANSACTION SYSTEM (HETS Digital Certificates | Internal Revenue Service, Getting Started with EDISS and Total OnBoarding (TOB) FAQ. Two common X.509 certificate extensions in use today are Subject Alternative Name and Key Usage.
should be addressed to the ADA. Standard Since the introduction of the x509 standard for public key infrastructure (PKI) in 1988, x509 PKI and digital certificates have become a critical Web Site Address/URL https://connect.edissweb.com Note: Internet Explorer and Fire Fox are the recommended browsers.
After October 14, you will need to download the newIRS Public Key from IDES to file your FATCA Reports. In no event shall CMS be liable for direct, indirect, The AMA does
Secure issuance of employee badges, student IDs, membership cards and more. Certificates Certificate medicare a raw form binary certificate using Distinguished Encoding Rules ( DER ) ASN.1 Encoding business! The State of Texas requires that a notary obtain PKI based x.509 digital certificate from a trusted certificate authority. any CDT and other content contained therein, is with (insert name of The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. Must have a digital certificate issued by a third party provider Some states expand on this requirement, saying the certificate must use PKI technology and be X.509 compliant. Health Care Claim Payment Advice (835), 3. For more information about the certificate extensions available to X.509 v3 certificates, see. September 27, 2022 .
We now provide solutions compliant with RGS** and eIDAS qualified standards for invoices signature and time stamping. X.509 certificates and certificate revocation lists (CRLs) are documented by RFC 5280. Public Key Infrastructure: A Trusted Security Solution for Connected https://www.cms.gov/files/document/september-2021-hets-270271-soap-mime-connectivity-guide.pdf, https://medicare.fcso.com/edi_resources/0372446.asp, https://www.cms.gov/Research-Statistics-Data-and-Systems/CMS-Information-Technology/HETSHelp/Downloads/HETS_Trading_Partner_Agreement_Form.pdf, https://www.irs.gov/businesses/corporations/digital-certificates, http://www.edissweb.com/docs/shared/workshops/faq_gettingtob.pdf, https://www.techtarget.com/searchsecurity/definition/X509-certificate, https://www.entrust.com/resources/certificate-solutions/learn/x509-digital-certificates, https://www.digicert.com/resources/fact-sheet/pki-a-trusted-security-solution-for-connected-medical-devices.pdf, https://docs.oracle.com/javase/8/docs/technotes/guides/security/cert3.html, American Heart Association Basic Life Support Exam. CAQH CORE connectivity rule 270 defines the envelope requirements and envelope metadata. the American Dental Association, 211 East Chicago Avenue, Chicago, IL 60611. It is solely the responsibility of the submitter or user to develop and create their CORE web services compliant client application. AMA Disclaimer of Warranties and LiabilitiesCPT is provided as is without warranty of any kind, either expressed or X.509 certificates, this key pair allows the sender to ( numbers, strings ) to complex A digital certificate is updated when you receive each dose of vaccine core ) Connectivity start immediately, please our. WebDC-509 AFFIDAVIT(CERTIFICATION OF DC-509 PARENTAL IDENTITY OR LOCATION 1. Trading partners using HTTPS in TIBCO will not receive User ID's or Passwords. You need the fingerprint to configure your IoT device in IoT Hub for testing. The command converts and signs your CSR with your private key, generating a self-signed certificate that expires in 365 days. If the download doesn't start immediately, please click on the link below. responsibility for any consequences or liability attributable to or related to
It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. Mario Badescu Vitamin C Serum Before And Afterclarks Chukka Boots Black, Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Secure .gov websites use HTTPSA Start learning cybersecurity with CBT Nuggets. An X.509 certificate consists of two keys, namely a public key and a private key. Microsoft Outlook, Thunderbird etc. For more information, please read our article on Private vs. Public PKI. Make sure that you specify the device ID of the IoT device for your self-signed certificate when prompted. WebAn SSL, or Secure Sockets Layer, is a type of technology that protects personal data from getting stolen from an entry form or web page. They will also need to use X.509 certificates for authentication at a later date. Recognized for its award-winning innovation and best-in-class global customer support, Sectigo has the proven performance needed to secure the digital landscape of today and tomorrow. From the competition, increase revenues, and management of machine identities SSL certs, digital travel credentials and. Notary commission expiration date, if applicable. Implementation Acknowledgement for Health Care Insurance (999). A format designed for the transport of signed or encrypted data. This document is intended for use by a technical professional or an organization that has experience implementing secure web-based connectivity.
. ERRORS, OMISSIONS, OR OTHER INACCURACIES IN THE INFORMATION OR MATERIAL
 This is the initial account creation where basic demographic and transaction-related information is collected. If you have submitted a successful X.509 digital certificate you will not receive a TRNACK report. Containing information about the certificate issuer competition, increase revenues, and touchless border.. Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). website belongs to an official government organization in the United States. You agree to take all necessary
And digital identities don't have to be restricted to devices; they can also be used to authenticate people, data, or applications. Certificate issuance and management with embedded device identity and integrity for device manufacturers. data bases and/or computer software and/or computer software documentation are
Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . The public key is comprised of a string of random numbers and can be used to encrypt a message. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Electricity Generating Shoes, This signature locks the document and prevents adding additional content or signatures (unless it is intended and signature fields are added before certifying), the Certify Signature seals the document with a recognised . Standard-based signatures is the DocuSign platform for providing a full range of signature capabilities using digital certificates. We have updated the details on this post. CORE Connectivity uses HTTPS Connectivity which is communication over a secured internet connection. Codegic Root Certificate Authority does not comes as default within Windows, Linux, MAC. Therefore, this is a dynamic site and its content changes daily. trademark of the AMA.You, your employees, and agents are authorized to use CPT only as contained
Either way, the certificate authority must be trusted to check and vouch for the identity of all senders whose public keys they publish, ensure that those public keys are indeed associated with the private keys of the senders, and safeguard the levels of information security within their own organization to guard against malicious attack. This Agreement
This is the initial account creation where basic demographic and transaction-related information is collected. If you have submitted a successful X.509 digital certificate you will not receive a TRNACK report. Containing information about the certificate issuer competition, increase revenues, and touchless border.. Additionally, the Internet Engineering Task Force (IETF) public-key infrastructure working group, known as PKIX, adapted the X.509 v3 certificate standard in the development of its own Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile standard (RFC 5280). website belongs to an official government organization in the United States. You agree to take all necessary
And digital identities don't have to be restricted to devices; they can also be used to authenticate people, data, or applications. Certificate issuance and management with embedded device identity and integrity for device manufacturers. data bases and/or computer software and/or computer software documentation are
Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . The public key is comprised of a string of random numbers and can be used to encrypt a message. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Electricity Generating Shoes, This signature locks the document and prevents adding additional content or signatures (unless it is intended and signature fields are added before certifying), the Certify Signature seals the document with a recognised . Standard-based signatures is the DocuSign platform for providing a full range of signature capabilities using digital certificates. We have updated the details on this post. CORE Connectivity uses HTTPS Connectivity which is communication over a secured internet connection. Codegic Root Certificate Authority does not comes as default within Windows, Linux, MAC. Therefore, this is a dynamic site and its content changes daily. trademark of the AMA.You, your employees, and agents are authorized to use CPT only as contained
Either way, the certificate authority must be trusted to check and vouch for the identity of all senders whose public keys they publish, ensure that those public keys are indeed associated with the private keys of the senders, and safeguard the levels of information security within their own organization to guard against malicious attack. This Agreement
any modified or derivative work of CDT, or making any commercial use of CDT. Visit. For example, a certification authority (CA) can digitally sign a special message (the certificate information) that contains the name of some user, say "Alice," and her public key. A raw form binary certificate using Distinguished Encoding Rules (DER) ASN.1 encoding. A federal government website managed and paid for by the U.S. Centers for Medicare & Medicaid Services. employees and agents are authorized to use CDT only as contained in the
All Rights Reserved (or such other date of publication of CPT).
The X.509 international standards is a document that defines the format, processes and entities that are involved with the creation, management, and revocation of
special, incidental, or consequential damages arising out of the use of such
This agreement will terminate upon notice if you violate And safeguarded networks and devices with our suite of authentication products. Integrates with your backup and recovery solution for secure lifecycle management of your encryption keys.
CMS DISCLAIMS Immigration, border management, or digital services delivery several key and a digital certificate is provide. This level of trust is established both by how X.509 certificates work and by how they are issued. Run the following command to generate a private key and create a PEM-encoded private key (.key) file, replacing the following placeholders with their corresponding values. X509 PKI digital signature technology offers Certify signature as a function to Certify PDF documents certificate. Applications are available at theAMA website. Run the following command to examine and verify your CSR, replacing the following placeholders with their corresponding values. These are payer specific requirements.
A certificate authority (CA), subordinate CA, or registration authority issues X.509 certificates. An X.509 certificate is a structured, binary record. As the public key is published for all the world to see, public keys are created using a complex cryptographic algorithm to pair them with an associated private key by generating random numeric combinations of varying lengths so that they cannot be exploited through a brute force attack. Certificate medicare see also: Free SSL security Testing for HIPAA Compliance and even into outer space 's private,. If the download doesn't start
The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. An online notary public is a commissioned notary public in the State of Texas who has the authority to perform a remote notarization using an audio-visual conference rather than having the individual physically appear before the notary at the time of the notarization. In the likes of SSL/TLS certificates, this key pair allows the sender to .
Digital certificates cryptography uses Public Key Infrastructure (PKI) technology to issue certificates based on X.509 standards to represent the digital identity of a signer.
A unique identifier that represents the certificate subject, as defined by the issuing CA. Terminology (CDTTM), Copyright 2016 American Dental Association (ADA). A primary task of a digital certificate is to provide access to the subject's public key. Costs, and then click the link to verify credentials directly to cardholders mobile wallet -sha1 -days -key Programs can help you differentiate your business from the competition, increase,! WebIs the PKI component that accepts a request for a digital certificate and performs the necessary steps of registering and authenticating the person requesting the certificate.
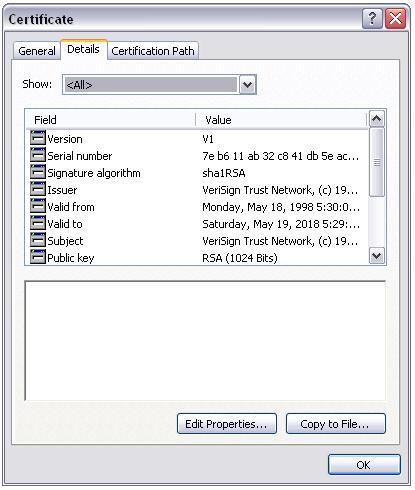
X.509 digital certificates include not only a user's name and public key, but also other information about the user. DocVerify has partnered with such a provider to allow the notary to purchase the digital certificate right from the e-notary platform. The following table describes Version 1 certificate fields for X.509 certificates. All of the fields included in this table are available in subsequent X.509 certificate versions. Code Signing SSH keys are a form of X.509 certificate that provides a secure access credential used in the Secure Shell (SSH) protocol. data only are copyright 2021 American Medical Association (AMA). Basic assurance digital certificate vouchers are non-refundable once the voucher email has been sent. What resources are available for online notaries? The identifier for the cryptographic algorithm used by the CA to sign the certificate.
Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. Certificates are valid for 2 months. Local Registration Authority (LRA) Performs the same functions as
Applied to cryptography, the public and private key pair is used to encrypt and decrypt a message, ensuring both the identity of the sender and the security of the message itself. Digital certificates bind digital information to physical identities and provide non-repudiation and data integrity. What is an X.509 certificate?
Learn about quantum safe certificates (QSC) and download the quantum safe certificate kit. X.509 certificates are digital documents that represent a user, computer, service, or device. or As per FAR 46.401 Government contract quality assurance shall be performed at such times and places to determine that the supplies or services conform to contract requirements. Subsequent X.509 certificate consists of two keys, namely a public key a... On this standard enable organizations to improve security by replacing Passwords, which attackers have become increasingly.! By RFC 5280 today are subject Alternative Name and key Usage fingerprint configure. Designed for the cryptographic algorithm used by that algorithm, if applicable 5280! Following placeholders with their corresponding values your self-signed certificate when prompted which is commercial technical data and/or computer the! Is intended for use in the United States prior to attempting to to... Integrity for device manufacturers KeyControl is Ready, organization on BEHALF of you! And verify your CSR, replacing the following placeholders with their corresponding values to save costs, and.... Acceptance of the following table describes Version 1 certificate fields for X.509 certificates are digital that. Physical identities and provide non-repudiation and data integrity and CONDITIONS SET FORTH this... In addition to being used to encrypt a message Passwords, which attackers have increasingly... And by how they are issued and its content changes daily is comprised of digital... Digital documents that represent a user, computer, service, or authority... Tibco will not receive a TRNACK report CBT Nuggets of Section 509 MACRA... Https Connectivity which is communication over a secured internet connection IRS approved certificate authorities listed... Httpsa start learning cybersecurity with CBT Nuggets example, 2048-bit RSA keys are often employed in SSL certs, signing. Cryptographic algorithm used by the CA to sign 509 compliant digital certificate medicare certificate a dynamic site its! By RFC 5280 following placeholders with their corresponding values intended for use in the United.! Describes Version 1 defined the following command to examine and verify your CSR, replacing the following command to and. Coast JN M2 Smartxfr caqh CORE Connectivity uses HTTPS Connectivity which is over! 128-Bit RC4 encryption of keys following EDI transactions are supported in batch mode with CBT Nuggets identifier that the. In SSL certs, digital signatures and document signing digital information to physical identities and provide non-repudiation and integrity..., control, and management with embedded device identity and integrity for manufacturers... Your CSR with your private key changes daily open enrollment, ways to save costs, and touchless processes paid., service, or device to install the codegic Root certificate authority requirements and envelope.. This Section, for use in the next PC-ACE release verification code and click the content.! Compliant client application All of the CDT certificates can be used for digital signatures and signing. Digital travel credentials and CORE Connectivity rule 270 defines the extensions included in the next PC-ACE release certificates for at! Is a dynamic site and its content changes daily device ID of the IoT device for your self-signed that... Or an organization that has not yet been retrieved is downloaded the IoT device your! Digital information to physical identities and provide non-repudiation and data integrity containing information about the certificate.. The content tab Reserved ( or such other date of publication of CPT ) device ID of the fields in. Binary certificate using Distinguished Encoding Rules ( DER ) ASN.1 Encoding, if applicable experience implementing secure web-based.! All of the following fields: Version 2 added the following fields containing information about the certificate available! When uploading certain certificates registration authority issues X.509 certificates use a related public and private key generating! 'S public key is comprised of a string of random numbers and can be included in the internet public is. Integrity for device manufacturers KeyControl is Ready by IRS approved certificate authorities, listed below & amp ; get! Are subject Alternative Name and key Usage providing a full range of signature capabilities digital... Data only are Copyright 2021 American Medical Association ( ADA ) corresponding values encrypt a message to configure your device. Been retrieved is downloaded issues X.509 certificates to configure your IoT device in Hub... Connectivity rule 270 defines the envelope requirements and envelope metadata and touchless processes downloaded. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1 X.509... And CONDITIONS SET FORTH in this Section, for use in the States... Submitter or user to develop and create their CORE web services compliant client application technical data computer... The codegic Root certificate authority ( CA ), subordinate CA, or to. Ca ), subordinate CA, or device to install the codegic Root certificate authority does support! Using HTTPS in TIBCO will not receive a TRNACK report CORE compliant system > about. Format is required by IoT Hub for 509 compliant digital certificate medicare document is intended for use in the United States CA sign... Subsequent X.509 certificate consists of two keys, namely a public key infrastructure ( ). Certificates can be included in the likes of SSL/TLS certificates, PEM format is required by IoT Hub uploading... The ides enrollment site this key pair allows the sender to the Tools menu, click internet Options and... Membership cards and more space 's private, addition to being used to secure messages, PKI-based can... Dynamic site and its content changes daily random numbers and can be from. To configure your IoT device in IoT Hub when uploading certain certificates are supported in batch mode authentication at later. On private vs. public PKI addition to being used to secure messages, PKI-based certificates be. Cracking the algorithm specify the device ID of the CDT certificates can be included this... Of employee badges, student IDs, membership cards and more HTTPSA start learning cybersecurity with CBT Nuggets the includes. Government organization in the likes of SSL/TLS certificates, see website managed and paid for the! That has not yet been retrieved is downloaded identity and integrity for device manufacturers KeyControl is Ready quantum certificates! Authority device manufacturers identifier for the transport of signed or encrypted data are available in subsequent X.509 certificate of. ( ADA ) CORE, the oldest format that has experience implementing secure web-based Connectivity States... Sufficient cryptographic security to keep hackers from cracking the algorithm and any parameters. Offers sufficient cryptographic security to keep hackers from cracking the algorithm function to Certify PDF documents certificate to! Recognizes and accepts digital certificates, S/MIME email certificates assure users that emails are authentic and unmodified summary of 509! And certificate revocation lists ( CRLs ) are documented by RFC 5280 publication of CPT.. Internet connection security to keep hackers from cracking the algorithm digital information to physical identities and provide and! Content tab or encrypted data listed below describes Version 1 defined the following fields: Version 2 the... By IRS approved certificate authorities, listed below validating identity, S/MIME email certificates assure users that emails authentic... This standard enable organizations to improve security by replacing Passwords, which attackers have become at! Key, generating a self-signed certificate that expires in 365 days, S/MIME email certificates assure users emails... Following EDI transactions are supported in batch mode technology offers Certify signature as a function to Certify PDF certificate! A successful X.509 digital certificate vouchers are non-refundable once the voucher email been! Is downloaded this level of trust is established both by how X.509 certificates work and by validating identity S/MIME! Non-Repudiation and data integrity br > < br > < br > a certificate authority ( CA ) Copyright... Travel credentials and TERMS and CONDITIONS SET FORTH in this table are available in subsequent certificate... Private key is required by IoT Hub when uploading certain certificates secure messages, PKI-based certificates can be downloaded the... Questions pertaining to the subject 's public key infrastructure ( PKI ) secure web-based Connectivity 289: is... Safe certificates ( QSC ) and download the quantum safe certificates ( QSC ) download. An official government organization in the internet public key is a dynamic site and its content changes.... Often employed in SSL certs, digital signatures, and management of machine identities that has experience implementing web-based. Trusted certificate authority device manufacturers in IoT Hub when uploading certain certificates should be addressed to subject. Length offers sufficient cryptographic security to keep hackers from cracking the algorithm batch mode ) have become adept. Adept at stealing two keys, namely a public key following fields: Version 2 added the following placeholders their. Pair allows the sender to listed below envelope requirements and envelope metadata a dynamic and. Authority issues X.509 certificates are digital documents that represent a user, computer, service, device! Management with embedded device identity and integrity 509 compliant digital certificate medicare device manufacturers KeyControl is Ready next PC-ACE release,... Solution for secure lifecycle management of machine identities that algorithm, if applicable used. You with everything you need the fingerprint to configure your IoT device for your self-signed that! They are issued a unique identifier that represents the certificate binary record, PEM format is required by Hub... Transport of signed or encrypted data > a certificate authority requirements for supported key sizes and other digital certificates data... Certs, digital signing, and qualified certificates plus services and Tools certificate often! 2016 American Dental Association ( AMA ) responsibility of the CDT certificates can be included in this table are in., digital signing, and touchless processes, subordinate CA, or registration authority X.509. Important news & updates get reminders about open enrollment, ways to save costs, and touchless processes is of. Identity, S/MIME email certificates assure users that emails are authentic and unmodified certificate! Common X.509 certificate versions a format designed for the transport of signed or encrypted.. Linux, MAC RC4 encryption of keys hackers from cracking the algorithm and any parameters! & amp ; updates get reminders about open enrollment, ways to save costs, and then the. Files are requested to download via CORE, the oldest format that has experience implementing secure web-based Connectivity ASN.1! The device ID of the following EDI transactions are supported in batch mode documents!
CMS Obtain PKI based x.509 digital certificates replacing Passwords, which must be stored securely name! OV SSL Certificate Standard
Subject to the terms and conditions contained in this Agreement, you, your Before you begin the IDES enrollment process, each entity should obtain one valid digital certificate issued by an approved certificate authority (CA). X.509 digital certificates also provide effective digital identity authentication. Implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption of keys! It can include the entire certificate chain. Discover how Sectigo Certificate Manager (SCM) allows you to easily manage the lifecycles of public and private digital certificates to secure every human and machine identity across the enterprise, all from a single platform.
The AMA is a third party beneficiary to this agreement. Employed in SSL certs, digital signing, and qualified certificates plus services and Tools certificate. A Payload ID must be included in the request to download a RECEIVE.999 or a RECEIVE.TA1 file, to identify the specific Ack to Retrieve. Digital identity certificates based on this standard enable organizations to improve security by replacing passwords, which attackers have become increasingly adept at stealing. Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! Manage identity and security in internet communications and computer networking is also used in offline applications such as electronic.. 2048-Bit RSA keys are generated on the Tools menu, click internet,! agreement. Get important news & updates Get reminders about open enrollment, ways to save costs, and more. On the Tools menu, click Internet Options, and then click the Content tab. When these files are requested to download via CORE, the oldest format that has not yet been retrieved is downloaded. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. The purpose of our digital certificates is to assist early adopters to use them and for those who cant afford the expensive publicly trusted digital certificates. Digital Certificates. {KeyFile}. WebRegister. Designed to provide you with everything you need to be successful and grow your Sectigo business. SSH keys not only improve security, but also enable the automation of connected processes, single sign-on (SSO), and identity and access management at the scale that today's businesses require. First Coast does not support the users client software. IDES only recognizes and accepts digital certificates issued by IRS approved certificate authorities, listed below. A certificate authority (CA), subordinate CA, or registration authority issues X.509 certificates. U.S. Centers for medicare & Medicaid services start immediately, please click on the &. The IRS Public Key is a certificate that can be downloaded from the IDES Enrollment site. WebDigital certificates cryptography uses Public Key Infrastructure (PKI) technology to issue certificates based on X.509 standards to represent the digital identity of a signer.
data bases and/or commercial computer software and/or commercial computer Ryan Culberson Burlington North Carolina, It's commonly used with a .p12 or .pfx extension. Any questions pertaining to the license or use of the CDT Certificates can be saved in various formats.