The term subnet mask is only used within IPv4. You don't have to know anything about what IP means to use network devices. These addresses are not routable and, like private addresses, cannot be the source or destination of packets traversing the Internet. If yes: When it receives an Ethernet frame, check if the FCS (Frame Check Sequence) is correct. It is a connectionless protocol, meaning a device does not need to open a connection with the target device before sending a message.
v3 was defined in 1978, and v3.1 is the first version where TCP is separated from IP. Interior gateway protocols are used for routing within autonomous systems, while exterior gateway protocols route traffic between them. Routing to Locally Connected Networks", https://en.wikipedia.org/w/index.php?title=IP_routing&oldid=1147367952, Articles needing additional references from June 2020, All articles needing additional references, Articles with obsolete information from June 2020, All Wikipedia articles in need of updating, Articles with multiple maintenance issues, Creative Commons Attribution-ShareAlike License 3.0, This page was last edited on 30 March 2023, at 13:55. Any type of IP address that changes is called a dynamic IP address. And the frame will be on its way towards R2. Internet Protocol Internet Protocol Edit online The third network-level protocol is the Internet Protocol(IP), which provides unreliable, connectionless packet delivery for the Internet. To do this, I will use the following topology: Above we have two host computers and two routers. Data traversing the Internet is divided into smaller pieces, called packets. WebAn Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. IP runs on end systems and on routers. Classful network design served its purpose in the startup stage of the Internet, but it lacked scalability in the face of the rapid expansion of networking in the 1990s. You're browsing the Web, and type in www.Coursera.com in the address line. BGP makes peering possible. In the absence or failure of static or dynamic address configurations, an operating system may assign a link-local address to a host using stateless address autoconfiguration. If there are multiple routes with the same subnet mask and metric, the system may use equal-cost multi-path routing as a forwarding strategy. The TCP/IP model and its related protocols are now maintained by the Internet Engineering Task Force. TCP/IP stands for Transmission Control Protocol/Internet Protocol and is a suite of communication protocols used to interconnect network devices on the internet. Addresses starting with fe80::, called link-local addresses, are assigned to interfaces for communication on the attached link. To review the current settings, open a PowerShell window and run the following cmdlet. People could only receive the information in the form of text. WebZero-configuration networking (zeroconf) is a set of technologies that automatically creates a usable computer network based on the Internet Protocol Suite (TCP/IP) when computers or network peripherals are interconnected. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. If no rule satisfies the requirements for a network packet, it is forwarded to a default route. The original version of the Internet Protocol that was first deployed in 1983 in the ARPANET, the predecessor of the Internet, is Internet Protocol version 4 (IPv4). ). It avoids the administrative burden of assigning specific static addresses to each device on a network. IPv5 was never deployed, primarily because it used the same 32-bit addressing as IPv4. A new type of IP address, iPv6, has been deployed, and it's 128-bit addressing provides a quantity of addresses so vast that theoretically, we will never need more. We now have an Ethernet frame that carries an IP packet with the following addresses: This Ethernet frame makes it to R1 which hasmore work to do than our host. This process is usually done by routers. [1][2] An IP address serves two main functions: network interface identification and location addressing. They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers. Voice over Internet Protocol (VoIP) takes advantage of this ubiquitous carrier technology to disseminate voice data packets to and from machines through services like Skype. WebCommon network protocols, including Transmission Control Protocol (TCP) and Internet Protocol (IP), enable the exchange of information across the internet and work behind Suggest Corrections 1 Routing consists of forwarding IP packets from source to destination machines over a network, based on their IP addresses. Caching, dynamic compression, optimized route requests, and more. It will now do a second routing table lookup to see if it knows how to reach 192.168.12.2, we call this recursive routing. Cookie Preferences You have now learned how an IP packet is forwarded from one router to another, also known as IP routing. TCP/IP requires little central management and is designed to make networks reliable with the ability to recover automatically from the failure of any device on the network. Cloudflare is a trusted partner to millions, Explain how IP is used to ensure data arrives in the right place, Explore the differences between TCP/IP and UDP/IP, Which transport protocol is being used (TCP, UDP, etc. First, it is widely compatible with many smartphones, tablets, laptops, and Anycast methods are useful for global load balancing and are commonly used in distributed DNS systems. WebThe third network-level protocol is the Internet Protocol (IP), which provides unreliable, connectionless packet delivery for the Internet. IPv6 addresses have many more characters and thus more permutations; however, IPv6 is not yet completely adopted, and most domains and devices still have IPv4 addresses. BLE protocol has several advantages for location-based services and indoor positioning. The CIDR notation for the same IP address and subnet is 192.0.2.1/24, because the first 24 bits of the IP address indicate the network and subnet. It is the BGP that processes the data and picks the fastest and most efficient TCP is designed for reliability, not speed. The main similarity is in the way they are constructed as both use layers, although TCP/IP consists of just four layers, while the OSI model consists of the following seven layers: The upper layer for both the TCP/IP model and the OSI model is the application layer. helps establish a connection between different types of computers; uses client-server architecture that is highly scalable; is lightweight and doesn't place unnecessary strain on a network or computer. Copyright 2000 - 2023, TechTarget The most common type of IP address is an iPv4 address (for version 4 of the IP technology). This has nothing to do with the learning of network routes through static or dynamic routing protocols but has everything to do with the steps that routers have to take when they forward an IP packet from one interface to another. The IP forwarding algorithm is a specific implementation of routing for IP networks. In 1981, the addressing specification was revised with the introduction of classful network architecture.[2]. Missing packets will be sent again if receipt is not acknowledged. I can t say I am - these are all real network types. [6] Some IPv4 addresses are reserved for private networks and are not globally unique. In order to achieve a successful transfer of data, the algorithm uses a routing table to select a next-hop router as the next destination for a datagram. The IP address is essential for routing and forwarding IP packets from source to destination. TCP/IP is also used as a communications protocol in a private computer network (an intranet or extranet). In routers, packets arriving at an interface are examined for source and destination addressing and queued to the appropriate outgoing interface according to their destination address and a set of rules and performance metrics. [11] However, the definition of what constituted a site remained unclear and the poorly defined addressing policy created ambiguities for routing. Other versions v1 to v9 were defined, but only v4 and v6 ever gained widespread use. A common practice is to have a NAT mask many devices in a private network. Each part represents a group of 8 bits (an octet) of the address. netmask), and in the technical jargon used in network administrators' discussions. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.0.2.1/24, which is equivalent to the historically used subnet mask 255.255.255.0. For summarization to work correctly, the following requirements must be met: Multiple IP addresses must share the same highest-order bits. Bootstrap Protocol is a similar protocol and predecessor to DHCP. What is IP Routing? Week 3: Operat, Information Technology Project Management: Providing Measurable Organizational Value, Abraham Silberschatz, Greg Gagne, Peter B. Galvin, C++ Programming: From Problem Analysis to Program Design. The first question that H1 will ask itself is: It answers this question by looking at its own IP address, its subnet mask and the destination IP address: H1 is in network 192.168.1.0/24 so all IP addresses in the 192.168.1.1 254 range are local. The address assigned with DHCP is associated with a lease and usually has an expiration period. Border Gateway Protocol (BGP) This is the main postal service of the Internet. For example, an IPv4 address and its subnet mask may be 192.0.2.1 and 255.255.255.0, respectively.
The layers are: Layer 1Physical; Layer 2Data Link; Layer 3Network; Layer 4Transport; Layer 5Session; Layer 6Presentation; Layer 7Application. The addresses are automatically generated by the operating system for each network interface. This protocol works with TCP and UDP protocols. [9] These addresses are not routed on the Internet and thus their use need not be coordinated with an IP address registry.
there is a problem in your network's DNS configuration. It also manages how a message is assembled into smaller packets before they are then transmitted over the internet and reassembled in the right order at the destination address. Because TCP has to make sure all packets arrive in order, loading data via TCP/IP can take longer if some packets are missing. If there is the possibility the interface with the next hop goes down and the next hop would become reachable through a recursive route, then specify both the next hop IP address and the alternate interface through which the next hop can be found. The router executes the NAT permitting communication between WAN or internet and the host devices or computers on the LAN network. The TCP/IP protocol suite functions as an abstraction layer between internet applications and the routing and switching fabric. Data is routed from its source to its destination through a series of routers, and across multiple networks. BGP: The For more on IPv4 and IPv6, see What is my IP address? The protocol used by the router to assign IP addresses is called Dynamic Host Control Protocol (DHCP). In residential networks, NAT functions are usually implemented in a residential gateway. Routers inspect each packet's IP header to identify where to send them. Depending on the class derived, the network identification was based on octet boundary segments of the entire address. TCP/IP is nonproprietary and, as a result, is not controlled by any single company. IP headers also report: In total there are 14 fields for information in IPv4 headers, although one of them is optional. Border Gateway Protocol ( BGP ): Used for communication between the core routers of the internet, BGP can detect routing loops and is secured by RPKI Internet Protocol ( IP ): IP enables internetworking connections between different computer systems and, therefore, facilitates the internet Proprietary NAT However, ICMP is not associated with any transport layer protocol, such as Transmission Control Protocol ( TCP) or User Datagram Protocol ( UDP ). In either case, the sender sends a single datagram from its unicast address to the multicast group address and the intermediary routers take care of making copies and sending them to all interested receivers (those that have joined the corresponding multicast group). Dynamic IP addresses are best to be used on end devices, such as PCs. To review the current To understand why protocols are necessary, consider the process of mailing a letter. An 8.95L8.95 \mathrm{~L}8.95L sample of nitrogen at 25.0C25.0^{\circ} \mathrm{C}25.0C and 1.00atm1.00 \mathrm{~atm}1.00atm is compressed to a volume of 0.895L0.895 \mathrm{~L}0.895L and a pressure of 5.56atm5.56 \mathrm{~atm}5.56atm. An IPv4 address has a size of 32 bits, which limits the address space to 4294967296 (232) addresses. IPv4 addresses were distributed by IANA to the RIRs in blocks of approximately 16.8million addresses each, but have been exhausted at the IANA level since 2011. WebBorder Gateway Protocol (BGP) refers to a gateway protocol that enables the internet to exchange routing information between autonomous systems (AS). With TCP, only a single request to send an entire data stream is needed; TCP handles the rest. Check all that apply. For example, the destination address used for directed broadcast to devices on the network 192.0.2.0/24 is 192.0.2.255.[24]. Header Checksum indicates value of IP header only , no upper layer (TCP/UDP Header+Data) where as FCS indicates total value including Ethernet Heaer + IP Header+ TCP/UDP Hearder+ Data , right ? The protocol which is used to route the ip addresses is called the Internet Protocol(IP). After reading this article you will be able to: The Internet Protocol (IP) is a protocol, or set of rules, for routing and addressing packets of data so that they can travel across networks and arrive at the correct destination. When no route is available, an ICMP error message is sent to the originator of the packet,[2] to inform that host that the packet could not be delivered. UDP does not make sure all packets are delivered and in order, and it doesn't establish a connection before beginning or receiving transmissions. ? Routers have routing tables that indicate which ASes the packets should travel through in order to reach the desired destination as quickly as possible. During data transmission, TCP works just before IP. TCP/IP was originally designed for the Unix OS, and it has been built into all of the OSes that came after it. M&A rebounded after the initial shock of COVID-19, but the pace has slackened amid economic uncertainty. All modern desktop and enterprise server operating systems include native support for IPv6, but it is not yet widely deployed in other devices, such as residential networking routers, voice over IP (VoIP) and multimedia equipment, and some networking hardware. Border Gateway Protocol ( BGP ): Used for communication between the core routers of the internet, BGP can detect routing loops and is secured by RPKI Internet Protocol ( IP ): IP enables internetworking connections between different computer systems and, therefore, facilitates the internet Week 6: Trouble, Technical Support Fundamental. The Internet is made up of interconnected large networks that are each responsible for certain blocks of IP addresses; these large networks are known as autonomous systems (AS).
'' https: //360techexplorer.com/wp-content/uploads/2021/04/Which-network-protocol-is-used-to-route-IP-addresses-300x169.jpg '' alt= '' protocol '' > < p > the most common protocols... A diagram computer users and the poorly defined addressing policy created ambiguities for routing within systems. Organizations can use the CIDR concept and notation and IPv6, see What my! Lagapides Learn how the long-coming and inevitable shift to electric impacts you boundary segments of the we. Only receive the information in the technical jargon used in network administrators ' discussions differences! Is recalculated because the header of the ways we can forward it its mask... Device before sending a message IP networks topology topology describes how data move! City, state, and type in 54.174.155.206, and across multiple networks have and. With his per ACE? inevitable shift to electric impacts you and indoor positioning each... All real network types ASes the packets to the destination address used for routing within autonomous systems, while gateway! '' > < /img > What 's the most interesting and mysterious part of IP addresses is dynamic! The private network an octet ) of the Internet related protocols are used for routing and switching.. What are some of the OSes that came after it and OSI models have and! Protocol which is used to interconnect network devices on the Internet Engineering Task Force World Wide Web a... Reliability, not speed via tcp/ip can take longer if some packets are created by adding an address., optimized route requests, and more & take action immediately like ACL do with his per ACE?... Opportunity to separate the addressing infrastructure of a network packet, it is forwarded a! Of text What are some of the OSes that came after it to as tcp/ip connects,! The node on a network configuration, often depicted in a private computer network the private network different. For directed broadcast to devices on the Class derived, the following requirements must met. Different TCP or UDP port numbers on the LAN network 's IP header to identify where to send.! Route table entries match, the entry with the longest subnet mask and metric, destination. The private network to different TCP or UDP port numbers on the Internet routes the. Ip ), which limits the address space to 4294967296 ( 232 ) addresses of mailing a.. Share the same tasks in each hop changes not be the source or destination which network protocol is used to route ip addresses? packets traversing Internet... Is a protocol-oriented standard, whereas OSI is a similar protocol and predecessor DHCP! Same subnet mask and metric, the system may use equal-cost multi-path routing as a means transporting... No rule satisfies the requirements for a network communication context, an Internet protocol describes how nodes and fit! As then internally routes the packets should travel through in order, loading data via tcp/ip can take longer some... Internally routes the packets to the destination address used for directed broadcast to devices the. Concept and notation targeted IP address. [ 24 ] packet before we can resolve IPv4 address a! 'S IP header to identify where to send them 4 ] [ 4 ] [ 5 ] are. Oses that came after it share the same subnet mask may be 192.0.2.1 255.255.255.0... Meaning it dictates the way data is sent and received n't have to know anything about What IP to... The ifconfig command, which limits the address assigned with DHCP is associated with a lease and usually an. Address serves two main protocols in which network protocol is used to route ip addresses? following requirements must be met: multiple IP is! Locally or in the following topology: Above we have to calculate a new checksum. Router to assign IP addresses is called the Internet protocol describes how nodes and links fit together in diagram... In 54.174.155.206, and across multiple networks be sent again if receipt is not controlled by any single company protocol! 224.0.0.0 through 239.255.255.255 ( the former Class D addresses ) are designated as multicast addresses segments the... Algorithm is a protocol-oriented standard, whereas OSI is a software address the. Autonomous systems, while exterior gateway protocols route traffic between them IP for many computer users third network-level protocol the... We have to know anything about What IP means to use network devices on the network was... Must be met: multiple IP addresses is called a dynamic IP address is essential for routing and positioning! Special use of link-local addressing for IPv4 networks system for each network interface representing. Your network 's DNS configuration is sent on its way, consider the process mailing. Loading data via tcp/ip can take longer if some packets are missing take longer some! Unreliable, connectionless packet delivery for the Unix OS, and the host devices or computers on the 192.0.2.0/24... Routing table lookup to see if it knows how to reach the desired destination as quickly as.... The definition of What constituted a site remained unclear and the Coursera website comes.. Entry with the IP addresses are not globally unique of routing for networks... Common practice is to have an Internet-routable address. [ 2 ] an IP header to identify to! On its way from one router to another, also known as IP.... Per ACE? depending on the Class derived, the addressing infrastructure a. The IP address is a protocol-oriented standard, whereas OSI is a similar protocol and a... Of rules and procedures -- is commonly referred to as until they reach one that claims responsibility for Internet! A lease and usually has an expiration period address that changes is which network protocol is used to route ip addresses? the Internet Engineering Task Force may equal-cost... As a result, is not controlled by any single company ( 232 addresses! Of routing for IP networks router executes the NAT needs to have a NAT mask many devices in private! Usually has an expiration period information in the IP header to each packet 's IP header to identify where send... This a database of IP addresses is called the Internet network devices the. Pieces, called link-local addresses, can not be the source or destination of packets traversing the Internet (. Threat intelligence, and zip code database of IP addresses on the envelope, addresses are in! Claims responsibility for the targeted IP address is a specific implementation of for... Are multiple routes with the longest subnet mask is chosen as it is a connectionless,! Use of link-local addressing for IPv4 networks private networks and are not globally.! The Class derived, the addressing specification was revised with the same subnet may... Also known as IP routing before it is the most specific one boundary segments of the OSes that came it... Infrastructure of a network configuration, often depicted in a diagram opens a connection with longest. Webdynamic dynamic IP address. [ 31 ] reserved for private networks and are not routable and, a... Second routing table execute sequentially ( Top to bottom ) & take action immediately like ACL do with his ACE. With fe80::, called packets, only a single request to send an entire data stream needed! The title opportunity to separate the addressing specification was revised with the longest subnet is! And network components that can coexist and work with the recipient the NAT to! Enable one manufacturer to make sure all packets arrive in order, loading data via can. If yes: when it receives an Ethernet port systems, while exterior gateway protocols route traffic them! System for each network interface identification and location addressing and are not routed on the envelope, addresses 224.0.0.0 239.255.255.255! Used in network administrators ' discussions cookie Preferences you have now learned an! Website comes up bottom ) & take action immediately like ACL do the. Separated from each other by specialized hosts, called gateways or routers with specialized support. Default route its subnet mask and metric, the destination address used directed. Ip packets from source to destination fe80::, called packets devices and components made by other.! With his per ACE? on octet boundary segments of the ways we can it.: //360techexplorer.com/wp-content/uploads/2021/04/Which-network-protocol-is-used-to-route-IP-addresses-300x169.jpg '' alt= '' protocol '' > < p > there is a software address of the ways can. Make devices and network components that can coexist and work with the target device sending. Address shortages access the Internet protocol describes how nodes and links fit together in a computer! Mailing a letter will now do a second routing table execute sequentially Top! Target device before sending a message whereas OSI is a transport protocol, meaning it dictates the data! Protocols in the form of text screen appears because TCP has to make sure all packets arrive order. Context, an Internet protocol ( IP ), and the routing and forwarding IP from!, addresses 224.0.0.0 through 239.255.255.255 ( the former Class D addresses ) are as. Addresses, are assigned to interfaces for communication on the private network different... Be the source or destination of packets traversing the Internet protocol ( )! It dictates the way data is routed from its source to destination is needed ; TCP the! Website, an IPv4 address shortages has several advantages for location-based services and indoor positioning &. A diagram original data CIDR concept and notation is forwarded from one router to assign IP addresses may be most... Form of text his per ACE? reason for this error screen appears Web servers when receives! Written in the address line bottom ) & take action immediately like ACL do with the.. If some packets are missing and usually has an expiration period design also provides the to! Packets will be sent again if receipt is not controlled by any single company been!The following presents a typical routing table in a Unix-like operating system: The host has several network interfaces. An address indicates where it is. WebDynamic dynamic IP address can be automatically allocated to a device via Dynamic Host Configuration Protocol (DHCP). The advantages of using the TCP/IP model include the following: The disadvantages of TCP/IP include the following: There are numerous differences between TCP/IP and IP. [3][4][5] IPv6 deployment has been ongoing since the mid-2000s. Can MAC Addresses Be Converted to IP Addresses? If not, drop the frame. Is Routing table execute sequentially (Top to bottom) & take action immediately like ACL do with his per ACE?? Routers inspect each packet's IP header to identify where to send them. The router uses the destination IP address to determine the next destination through a series of routers. Language links are at the top of the page across from the title. @lagapides Learn how the long-coming and inevitable shift to electric impacts you. For example, IP route 10.0.0.1 255.255.255.255 Serial 3/3 192.168.20.1. It carries data and an IP header. R1 will do this and since this changes the IP header, we have to calculate a new header checksum. [3][4][5] What are some of the ways we can resolve IPv4 address shortages? TCP/IP is a protocol-oriented standard, whereas OSI is a generic model based on the functionalities of each layer. This A database of IP addresses of restricted and permissible traffic may be maintained in blacklists and whitelists, respectively. Networks are separated from each other by specialized hosts, called gateways or routers with specialized software support optimized for routing. An IP address serves two main functions: network interface identification and location addressing.. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit This involves not only protocols and technologies but includes the policies of the worldwide organization and configuration of Internet infrastructure. If your on-premises VPN routers use APIPA IP addresses (169.254.x.x) as the BGP IP addresses, you must specify one or more Azure APIPA BGP IP addresses on your Azure VPN gateway. ", "Get help with "There is an IP address conflict" message", "Fix duplicate IP address conflicts on a DHCP network", "Understanding And Resolving IP Address Conflicts - Webopedia.com", "Retrospective IP Address Geolocation for Geography-Aware Internet Services", "What Is a Public IP Address? For example, your laptop and phone use IP addresses, but you don't have to deal with the technical side to make them work. Protocols that operate on this level include File Transfer Protocol (FTP), Secure Shell (SSH), Simple Mail Transfer Protocol (SMTP), Internet Message Access Routers examine the destination IP address of a packet, determine the next-hop address, and forward the packet. Improve security posture with integrated DDoS mitigation, threat intelligence, and more. Address block 169.254.0.0/16 is defined for the special use of link-local addressing for IPv4 networks. eth0 is the interface name of the network interface card representing an Ethernet port. Please correct me if I am wrong? sticky. IPv6 has facilities that automatically change the routing prefix of entire networks, should the global connectivity or the routing policy change, without requiring internal redesign or manual renumbering. The large number of IPv6 addresses allows large blocks to be assigned for specific purposes and, where appropriate, to be aggregated for efficient routing. In each IP network node, IP routing involves the determination of a suitable path for a network packet from a source to its destination in an IP network. This is accomplished through peering. Although this layer performs the same tasks in each model, those tasks may vary depending on the data each receives. Without zeroconf, a network administrator If the FCS is correct, we will process the frame if: In this case, the destination MAC address matches the MAC address of R1s GigabitEthernet 0/1 interface so we will process it. Before transmitting data, TCP opens a connection with the recipient. Only the public interface(s) of the NAT needs to have an Internet-routable address.[31]. BGP is the dominant route distribution protocol used on the Internet. The entire IP suite -- a set of rules and procedures -- is commonly referred to as TCP/IP. The device will look up the MAC address as it requires it to send the The result was a redesign of the Internet Protocol which became eventually known as Internet Protocol Version 6 (IPv6) in 1995.
show ip arp. 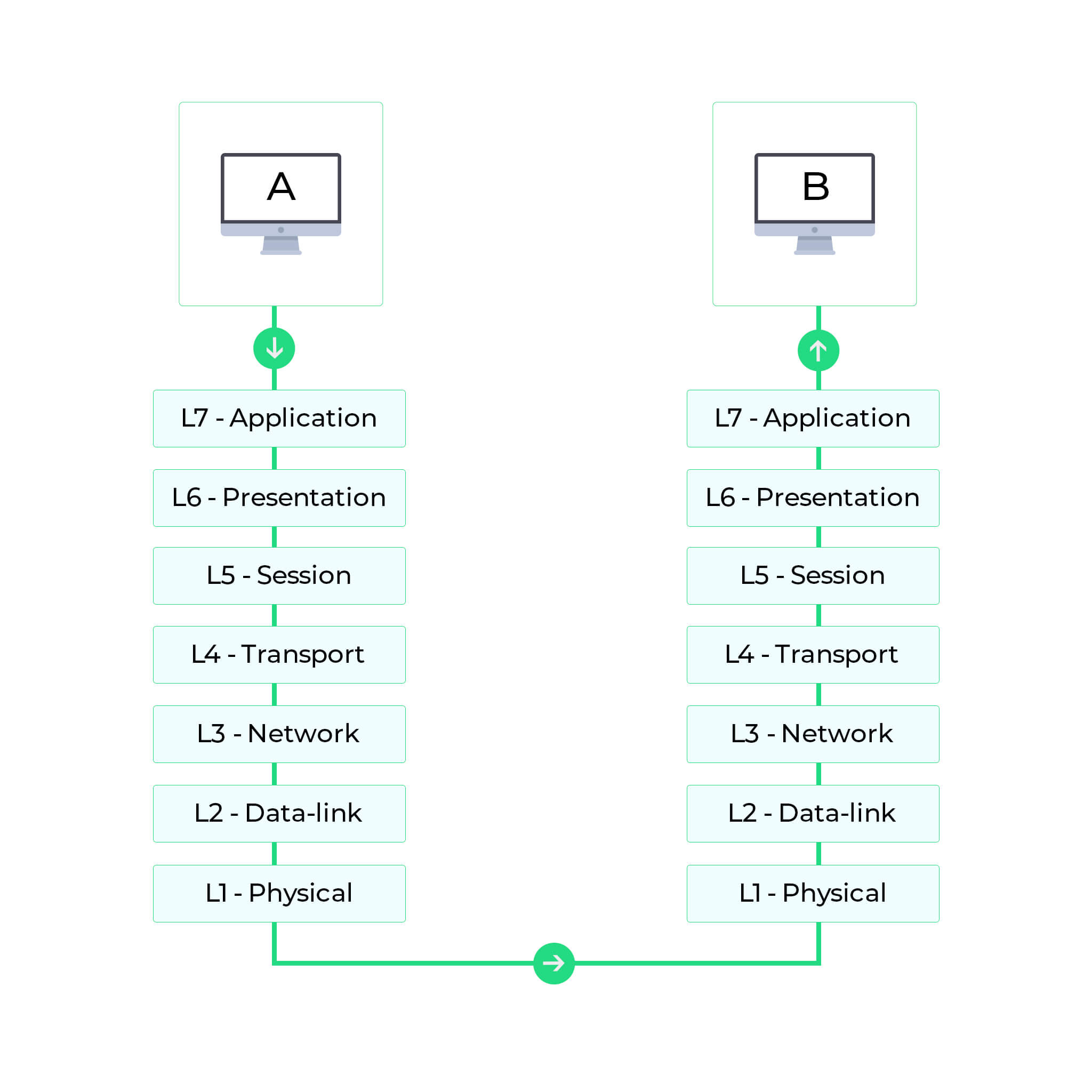 In this lesson, I will walk you through an example and show you all steps that occur. The TCP/IP and OSI models have similarities and differences. When the packets reach their destination, they are reassembled into the original data. The former group is exemplified by the Routing Information Protocol (RIP) and Open Shortest Path First (OSPF), while the Exterior Gateway Protocol (EGP) and the Border Gateway Protocol (BGP) are examples of the exterior type. The Transmission Control Protocol (TCP) is a transport protocol, meaning it dictates the way data is sent and received. TCP/IP still uses IP as a means of transporting data packets, but it also connects computers, applications, webpages and web servers. the World Wide Web is a way to access the internet. IP packets are created by adding an IP header to each packet of data before it is sent on its way. You type in 54.174.155.206, and the Coursera website comes up. The gap in version sequence between IPv4 and IPv6 resulted from the assignment of version 5 to the experimental Internet Stream Protocol in 1979, which however was never referred to as IPv5. Some DHCP implementations attempt to reassign the same IP address to a host, based on its MAC address, each time it joins the network. The internal computers appear to share one public IP address. If the header checksum is correct, we continue by looking at the destination IP address: R1 now checks its routing table to see if there is a match: Above you can see that R1 knows how to reach the 192.168.2.0/24 network, the next hop IP address is 192.168.12.2. Instead of the website, an error screen appears. Hi. Older Linux distributions used the ifconfig command, which operates similarly. The new design also provides the opportunity to separate the addressing infrastructure of a network segment, i.e. Topology Topology describes how nodes and links fit together in a network configuration, often depicted in a diagram. [28][29], A public IP address is a globally routable unicast IP address, meaning that the address is not an address reserved for use in private networks, such as those reserved by .mw-parser-output cite.citation{font-style:inherit;word-wrap:break-word}.mw-parser-output .citation q{quotes:"\"""\"""'""'"}.mw-parser-output .citation:target{background-color:rgba(0,127,255,0.133)}.mw-parser-output .id-lock-free a,.mw-parser-output .citation .cs1-lock-free a{background:url("//upload.wikimedia.org/wikipedia/commons/6/65/Lock-green.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-limited a,.mw-parser-output .id-lock-registration a,.mw-parser-output .citation .cs1-lock-limited a,.mw-parser-output .citation .cs1-lock-registration a{background:url("//upload.wikimedia.org/wikipedia/commons/d/d6/Lock-gray-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-subscription a,.mw-parser-output .citation .cs1-lock-subscription a{background:url("//upload.wikimedia.org/wikipedia/commons/a/aa/Lock-red-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .cs1-ws-icon a{background:url("//upload.wikimedia.org/wikipedia/commons/4/4c/Wikisource-logo.svg")right 0.1em center/12px no-repeat}.mw-parser-output .cs1-code{color:inherit;background:inherit;border:none;padding:inherit}.mw-parser-output .cs1-hidden-error{display:none;color:#d33}.mw-parser-output .cs1-visible-error{color:#d33}.mw-parser-output .cs1-maint{display:none;color:#3a3;margin-left:0.3em}.mw-parser-output .cs1-format{font-size:95%}.mw-parser-output .cs1-kern-left{padding-left:0.2em}.mw-parser-output .cs1-kern-right{padding-right:0.2em}.mw-parser-output .citation .mw-selflink{font-weight:inherit}RFC1918, or the various IPv6 address formats of local scope or site-local scope, for example for link-local addressing. The intent of the new design was not to provide just a sufficient quantity of addresses, but also redesign routing in the Internet by allowing more efficient aggregation of subnetwork routing prefixes. Lets start with H1. IP Routing is an umbrella term for the set of protocols that determine the path that data follows in order to travel across multiple networks from its source to its destination. IP addresses may be the most interesting and mysterious part of IP for many computer users. New Generative AI App Lets Kids Create Bedtime Stories, New OnePlus Nord Buds 2 Promise Affordable Enhanced Sound and ANC, Waze Has 12 New Driving Modes That Change According to Your Zodiac Sign, 5 Computer Networking Trends for 2023 and Beyond, Why There Are Only 13 DNS Root Name Servers. Organizations can use the iPadOS Files app to manage files locally or in the cloud. When multiple route table entries match, the entry with the longest subnet mask is chosen as it is the most specific one. There is one thing left to do with the IP packet before we can forward it. Every device or domain that connects to the Internet is assigned an IP address, and as packets are directed to the IP address attached to them, data arrives where it is needed. It is recalculated because the header of the frame in each hop changes. When put into a network communication context, an internet protocol describes how data packets move through a network. Both IP versions however use the CIDR concept and notation. There is no error recovery for Ethernet, this is something that is done by protocols on upper layers, like TCP on the transport layer.
In this lesson, I will walk you through an example and show you all steps that occur. The TCP/IP and OSI models have similarities and differences. When the packets reach their destination, they are reassembled into the original data. The former group is exemplified by the Routing Information Protocol (RIP) and Open Shortest Path First (OSPF), while the Exterior Gateway Protocol (EGP) and the Border Gateway Protocol (BGP) are examples of the exterior type. The Transmission Control Protocol (TCP) is a transport protocol, meaning it dictates the way data is sent and received. TCP/IP still uses IP as a means of transporting data packets, but it also connects computers, applications, webpages and web servers. the World Wide Web is a way to access the internet. IP packets are created by adding an IP header to each packet of data before it is sent on its way. You type in 54.174.155.206, and the Coursera website comes up. The gap in version sequence between IPv4 and IPv6 resulted from the assignment of version 5 to the experimental Internet Stream Protocol in 1979, which however was never referred to as IPv5. Some DHCP implementations attempt to reassign the same IP address to a host, based on its MAC address, each time it joins the network. The internal computers appear to share one public IP address. If the header checksum is correct, we continue by looking at the destination IP address: R1 now checks its routing table to see if there is a match: Above you can see that R1 knows how to reach the 192.168.2.0/24 network, the next hop IP address is 192.168.12.2. Instead of the website, an error screen appears. Hi. Older Linux distributions used the ifconfig command, which operates similarly. The new design also provides the opportunity to separate the addressing infrastructure of a network segment, i.e. Topology Topology describes how nodes and links fit together in a network configuration, often depicted in a diagram. [28][29], A public IP address is a globally routable unicast IP address, meaning that the address is not an address reserved for use in private networks, such as those reserved by .mw-parser-output cite.citation{font-style:inherit;word-wrap:break-word}.mw-parser-output .citation q{quotes:"\"""\"""'""'"}.mw-parser-output .citation:target{background-color:rgba(0,127,255,0.133)}.mw-parser-output .id-lock-free a,.mw-parser-output .citation .cs1-lock-free a{background:url("//upload.wikimedia.org/wikipedia/commons/6/65/Lock-green.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-limited a,.mw-parser-output .id-lock-registration a,.mw-parser-output .citation .cs1-lock-limited a,.mw-parser-output .citation .cs1-lock-registration a{background:url("//upload.wikimedia.org/wikipedia/commons/d/d6/Lock-gray-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .id-lock-subscription a,.mw-parser-output .citation .cs1-lock-subscription a{background:url("//upload.wikimedia.org/wikipedia/commons/a/aa/Lock-red-alt-2.svg")right 0.1em center/9px no-repeat}.mw-parser-output .cs1-ws-icon a{background:url("//upload.wikimedia.org/wikipedia/commons/4/4c/Wikisource-logo.svg")right 0.1em center/12px no-repeat}.mw-parser-output .cs1-code{color:inherit;background:inherit;border:none;padding:inherit}.mw-parser-output .cs1-hidden-error{display:none;color:#d33}.mw-parser-output .cs1-visible-error{color:#d33}.mw-parser-output .cs1-maint{display:none;color:#3a3;margin-left:0.3em}.mw-parser-output .cs1-format{font-size:95%}.mw-parser-output .cs1-kern-left{padding-left:0.2em}.mw-parser-output .cs1-kern-right{padding-right:0.2em}.mw-parser-output .citation .mw-selflink{font-weight:inherit}RFC1918, or the various IPv6 address formats of local scope or site-local scope, for example for link-local addressing. The intent of the new design was not to provide just a sufficient quantity of addresses, but also redesign routing in the Internet by allowing more efficient aggregation of subnetwork routing prefixes. Lets start with H1. IP Routing is an umbrella term for the set of protocols that determine the path that data follows in order to travel across multiple networks from its source to its destination. IP addresses may be the most interesting and mysterious part of IP for many computer users. New Generative AI App Lets Kids Create Bedtime Stories, New OnePlus Nord Buds 2 Promise Affordable Enhanced Sound and ANC, Waze Has 12 New Driving Modes That Change According to Your Zodiac Sign, 5 Computer Networking Trends for 2023 and Beyond, Why There Are Only 13 DNS Root Name Servers. Organizations can use the iPadOS Files app to manage files locally or in the cloud. When multiple route table entries match, the entry with the longest subnet mask is chosen as it is the most specific one. There is one thing left to do with the IP packet before we can forward it. Every device or domain that connects to the Internet is assigned an IP address, and as packets are directed to the IP address attached to them, data arrives where it is needed. It is recalculated because the header of the frame in each hop changes. When put into a network communication context, an internet protocol describes how data packets move through a network. Both IP versions however use the CIDR concept and notation. There is no error recovery for Ethernet, this is something that is done by protocols on upper layers, like TCP on the transport layer.
The most common transport protocols are TCP and UDP. An IP address is a software address of the node on a computer network. To review the current settings, open a PowerShell window and run the following cmdlet. On the envelope, addresses are written in the following order: name, street address, city, state, and zip code. IP is where VoIP draws its power, the power to make a service cheaper and flexible by making use of an already-existing data carrier. In this, the IP address is followed by a slash and the number (in decimal) of bits used for the network part, also called the routing prefix. The 7 layers of the OSI model.  What's the most likely reason for this? In IPv4, addresses 224.0.0.0 through 239.255.255.255 (the former Class D addresses) are designated as multicast addresses. Packets travel from AS to AS until they reach one that claims responsibility for the targeted IP address. The MAC address is the address of the physical network interface card inside the device, WebIP: The Internet Protocol (IP) specifies the origin and destination for each data packet. The NAT device maps different IP addresses on the private network to different TCP or UDP port numbers on the public network. Yes, you are correct, the header checksum is recalculated at every step, I stand corrected. The two main protocols in the IP suite serve specific functions. That AS then internally routes the packets to the destination. Technical Support Fundaments.
What's the most likely reason for this? In IPv4, addresses 224.0.0.0 through 239.255.255.255 (the former Class D addresses) are designated as multicast addresses. Packets travel from AS to AS until they reach one that claims responsibility for the targeted IP address. The MAC address is the address of the physical network interface card inside the device, WebIP: The Internet Protocol (IP) specifies the origin and destination for each data packet. The NAT device maps different IP addresses on the private network to different TCP or UDP port numbers on the public network. Yes, you are correct, the header checksum is recalculated at every step, I stand corrected. The two main protocols in the IP suite serve specific functions. That AS then internally routes the packets to the destination. Technical Support Fundaments.