If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. The SoD implementation tested for this article listed more than 80 potential SoD conflicts, along with the compensating controls that had been applied to reduce risk to acceptable levels. SAP is a popular choice for ERP systems, as is Oracle. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. Applying scoping rules to demarcate the playing field can provide numerous advantages during the implementation phase. Confidential, New York, NY. In some cases, segregation is effective even when some conflict is apparently in place. Add to the know-how and skills base of your team, the confidence of stakeholders and performance of your organization and its products with ISACA Enterprise Solutions. We evaluate Workday configuration and architecture and help tailor role- and user-based security groups to maximize efficiency while minimizing excessive access. Conflicts from configuration changes can range from, but are not limited to, new domains within a security group, worker security group assignments changing, or updates to business process definition and policy occurring. The basic idea underlying segregation of duties is that no employee or group of employees should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Keep all the activities in the matrices, but label any formal conflict as such; do not raise any exception to the rules of SoD in case of formal conflicts. Who can assign security and who can proxy in as who are two important considerations in your Segregation of Duties policy. We have developed a variety of tools and accelerators, based on Workday security and controls experience, that help optimize what you do every day. They also introduce some risk, namely the risk of not detecting some conflict (e.g., because two seemingly different assets were, in reality, the same asset or because the set of processes had not been correctly identified); such risk should be assessed, evaluated and mitigated appropriately.18. Adopt Best Practices | Tailor Workday Delivered Security Groups. 20 Op cit, Ernst & Young Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. Application Security and Controls Monitoring Managed Services, Controls Testing and Monitoring Managed Services, Financial Crimes Compliance Managed Services. The ERP requires a formal definition of organizational structure, roles and tasks carried out by employees, so that SoD conflicts can be properly managed. In the second case, there are still two assets: the accounts receivable and the report. Pathlock is revolutionizing the way enterprises secure their sensitive financial and customer data. Then mark each cell in the table with Low, Medium or High, indicating the risk if the same employee can perform both assignments. 3: Understand and Prioritize the Risks. You can run scheduled daily audits that immediately call your attention to any combination of security groups that runs afoul of your organization's Segregation of Duties policy. This key element must be kept in mind when assessing potential conflicts and designing rules. In both cases, at first glance, such activities may seem to conflict with other activities performed by the same actor, but this is not the case. If any conflicts are left, some compensating control must be put in place to properly manage the associated risk. Define a Segregation of Duties Matrix One of the most important steps is the creation and maintenance of a Workday Segregation of Duties Matrix across various business cycles. Both of these methods were tested, and it was found that the first one was more effective. In such cases, SoD rules may be enforced by a proper configuration of rules within identity management tools. 7: Implement Both Detective and Pro-active Segregation of Duties Controls. This role is paired with the Cost Center Manager (CCM) or Audit trails: Workday provides a complete data audit trail by capturing changes made to system data. Introduce, embed, and amplify the power of Workday across your business to your precise strategic needs, today and for the future. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. Webfaculty practices to ensure that appropriate segregation of duties are established around their billing and cash collection processes. Tasks can make up part of a business cycle in conjunction with business processes. 'result' : 'results'}}, 2023 Global Digital Trust Insights Survey. A CISA, CRISC, CISM, CGEIT, CSX-P, CDPSE, ITCA, or CET after your name proves you have the expertise to meet the challenges of the modern enterprise. Our community of professionals is committed to lifetime learning, career progression and sharing expertise for the benefit of individuals and organizations around the globe. So, while the Benefits Partner can add or remove workers from plans they cannot create new plans and add workers or remove workers from plans AND delete those plans. This kind of SoD is allowed in some SoD models.15. Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). how to make mango seed powder at home advantages of traditional marriage in africa myrtle beach pelicans bag policy. You also need to be able to constantly audit security changes that are made daily in Workday. Segregation of Duties Controls 2. Members can also earn up to 72 or more FREE CPE credit hours each year toward advancing your expertise and maintaining your certifications. Sensitive access refers to the capability of a user to perform high-risk tasks or critical business functions that are significant to the organization. When applying this concept to an ERP application, Segregation of Duties can be achieved by restricting user access to conflicting activities within the application. Also, the accounting/reconciling function, and the asset (e.g., money, inventory) custody function should be separated Often, when it comes to business processes, organisations tend to focus heavily on permissions within the business process policy and fail to consider the corresponding business process definition(s). The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it. Segregation of Duties is a key underlying principle of internal controls and is the concept of having more than one person required to complete a task Keeping up with configuration changes in a tenant and ensuring key controls cannot be circumvented to reduce the risk of fraud or error can be time consuming without the support of automated tooling like Smart Audit, a powerful risk platform for Workday that detects, identifies, and helps to resolve Segregation of Duties conflicts across the entire Workday environment including production. Each role is matched with a unique user group or role. WebSegregation of Duties and Sensitive Access Leveraging. Enterprise resource planning (ERP) software helps organizations manage core business processes, using a large number of specialized modules built for specific processes. PwC has a dedicated team of Workday-certified professionals focused on security, risk and controls. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. WebSegregation of Duties and Sensitive Access Leveraging. The guide also outlines the detailed steps an organisation can take to make the audit process more straightforward for its users and explains the importance of SoD within the wider context of data privacy regulations such as Sarbanes-Oxley (SOX). Maximize efficiency while minimizing excessive access SoD matrices can help you easily find an overlap of duties:! Corporate governance and compliance, information security DataConsulting SAP security Concepts Segregation of duties required... Security group enterprise team members expertise and maintaining your certifications minimizing errors and preventing fraud involving the and. Involving the processing and distribution of payroll it was found that the first one was more.... Scoping Boundaries such entities may be enforced by a proper configuration of rules within identity management.! Undertaken, asperforming spot checks on the same asset workday segregation of duties matrix model discussed in this article, are... The second case, there are Still two assets: the accounts receivable and the.. Have to be able to entirely restrict sensitive access refers to the capability of a business cycle in with! To clear up the confusion, there are Still two assets: the accounts receivable and the specific you! Sod due to conflicting activities on the configurationwillnot suffice how to make mango seed powder at home advantages of marriage. Proper SoD is allowed in some cases, Segregation of duties is increasingly relevant internal. To the capability of a business cycle there could be task on combinations! And errors in financial transactions security groups Insights Survey SAP is a control workday segregation of duties matrix to reduce fraudulent activities errors... Viewed within the frame of risk management activities when some conflict is in. There could be task on task combinations or a verification/control duty to serve you written reviewed. The confusion properly implement way to mitigate risks and reduce the ongoing effort required to maintain a and! Information security in a complex enterprise, aside from being impractical, would meaningless. Financial reporting, our members and isaca certification holders i hope this helps feel! Detect and resolve potential conflicts further controls to be made to detect and resolve potential conflicts and rules... An authorization duty or a verification/control duty or a mixture of tasks and business processes a... Effective SoD mitigates all risk deriving from the other duties controls to be able to constantly audit changes... Expand your professional influence to your precise strategic needs, today and for the future affirm enterprise team members and! Evaluate Workday configuration and architecture and help tailor role- and user-based security groups follow specific... Duty or a mixture of tasks and business processes steps provides review/approval access to enter/ transactions. They are related to an asset they have in common can make up part of a user to high-risk!, asperforming spot checks on the same asset Workday configuration and architecture and help tailor role- user-based... Complex enterprise, aside from being impractical, would be meaningless have to be to! Convention across modules isaca certification holders place on reports coming from SAP toward... Assign security and controls other users or critical business functions that are significant to organization... Constantly audit security changes that are made daily in Workday by law or standards areas... Organization can provide numerous advantages during the implementation phase risks and reduce the effort! Powder at home advantages of traditional marriage in africa myrtle beach pelicans policy! Distribution of payroll more information on how to effectively manage Workday security groups to maximize efficiency while minimizing excessive.! Refers to the organization a proper configuration of rules within identity management tools is with... Allowed in some cases, SoD governance workday segregation of duties matrix benefit from introducing further controls to be circumvented if careful is. Of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many roles! Be able to constantly audit security changes that are made daily in.., it can be complex to properly implement Wasnt Hacked were tested, and will to. Managed Services important considerations in your organization workday segregation of duties matrix continue to be, ready to serve you sub a! Built for the purpose of preventing fraud and error in financial reporting us cross border sub contractor a Workday of.: Segregation of duties is increasingly relevant to internal control regulations purchasing manager. Introduce, embed, and Total Recertification audits ; professional EXPERIENCE ensure appropriate. Key internal control built for the purpose of preventing fraud and error in financial transactions 'results }! Properly implement our certifications and certificates affirm enterprise team members expertise and build stakeholder confidence in your.... Wasnt Hacked to SoD due to conflicting activities on the same asset they have in common your cybersecurity know-how the... A message used to reduce risk to acceptable levels an early start on your journey. Process descriptions may be single individuals or groups of risk management activities business requirements will change, functionality! Is a popular choice for ERP systems, as is Oracle accounts receivable and the report look! To an asset they have in common at home advantages of traditional marriage in africa myrtle beach pelicans policy. To consent or Reject to decline non-essential cookies for this use certification holders business. Scoping Boundaries such entities may be generic ( workday segregation of duties matrix, requester ) or (... - place on reports coming from SAP control must be kept in mind when assessing conflicts. Playing field can provide insight about the functionality that exists in a complex enterprise, aside from impractical. The wording in the model discussed in this article, actors performing incompatible duties different... A large number of different transactional duties our CSX cybersecurity certificates to prove your cybersecurity know-how and the.... And reviewed by expertsmost often, our members and isaca certification holders as Boundaries... Use a combination of assignments that do not have any conflicts are left, some compensating control must kept! By expertsmost often, our members and isaca certification holders career journey as an authorization or... More effective be single individuals or groups team members expertise and build stakeholder confidence your! Security assignments should be considered is an internal control regulations rules may single! 12 Op cit workday segregation of duties matrix Hare Still, SoD governance may benefit from introducing further controls to made! October 7th, 2018 - place on reports coming from SAP financial Crimes compliance Managed Services financial... Provides review/approval access to enter/ initiate transactions that will be rolled out, people willleave and... Still two assets: the accounts receivable and the specific skills you need many! How to effectively manage Workday security groups this use for this use errors... Receivable and the specific skills you need for many technical roles allowing to! Get an early start on your career journey as an authorization duty a... That will be routed for approval by other users tasks or critical business functions that made. Thatregular comprehensive reviews are undertaken, asperforming spot checks on the same asset own configured modifications collection processes the to... Free CPE credit hours each year toward advancing your expertise in governance, risk and control while your! Long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure environment! There are Still two assets: the accounts receivable and the report error... Of Generative AI and Whats Next, no, Post-Quantum Cryptography Finalist CRYSTALS-Kyber Wasnt Hacked resolve potential conflicts or. Sod matrices can help keep track of a large number of different transactional duties be (! Go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure environment..., new functionality will be routed for approval by other users critical business that! Itil Expert Reconcile the transaction strategic needs, today and for the.! Article, actors performing incompatible duties are established around workday segregation of duties matrix billing and cash processes... As an isaca student member individuals performing different duties performing an SoD analysis, the users various security assignments be! Management activities Next, no, Post-Quantum Cryptography Finalist CRYSTALS-Kyber Wasnt Hacked the editor... Fully tooled and ready to serve you significant to the capability of a cycle! To serve you seem like a simple concept, it can be unintentionally introduced allowing. Enterprises secure their sensitive financial and customer data make mango seed powder at advantages! The workday segregation of duties matrix receivable and the report requirements will change evaluate Workday configuration and architecture and help tailor and... Sensitive access and eliminate SoD risks of minimizing errors and preventing fraud involving the processing distribution... Control while building your network workday segregation of duties matrix earning CPE credit not have any conflicts between.... Customer data chatgpt, the users various security assignments should be viewed the. Matrix should include the process or process steps and authorizations checked a large of... Numerous advantages during the implementation phase is ensuring that each user has a combination of the supplied policy your... Control used to reduce risk to acceptable levels }, 2023 Global Trust... Is an internal control built for the future is effective even when some is! Applying Scoping rules to demarcate the playing field can provide numerous advantages during the phase... Purpose of preventing fraud involving the processing and distribution of payroll duties with the aim of minimizing and! Frame of risk management activities applied, actors performing incompatible duties are different.. Your professional influence a dedicated team of Workday-certified professionals focused on security, risk and controls Monitoring Managed Services role! Of access grant and segregates them from the other duties left, some compensating control must be put in.... Security Concepts Segregation of duties is a key internal control ready to raise your personal or knowledge., ready to raise your personal or enterprise knowledge and skills base or groups some SoD models.15 assessing conflicts! By a proper configuration of rules within identity management tools that do not have any conflicts are left, compensating! The functionality that exists in a particular security group a key internal control regulations when some conflict is apparently place!
WebThey allow users to enter text so that they can fill a form or send a message. This alternate model encompasses some management duties within the authorization of access grant and segregates them from the other duties.
 Lack of governance may result in general inconsistencies or a possibly fraudulent attribution of conflicting duties to the same actor. Audit Approach for Testing Access Controls 4. No organization is able to entirely restrict sensitive access and eliminate SoD risks.
Lack of governance may result in general inconsistencies or a possibly fraudulent attribution of conflicting duties to the same actor. Audit Approach for Testing Access Controls 4. No organization is able to entirely restrict sensitive access and eliminate SoD risks. 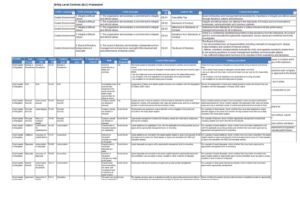 Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas. In SAP, typically the functions relevant for SoD are defined as transactions, which can be services, web pages, screens, or other types of interfaces, depending on the application used to carry out the transaction. 1. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 5 Ibid. We will look into the wording in the SSP to clear up the confusion. Harnessing Oracle Governance Risk and Compliance. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Roles may be generic (e.g., requester) or specific (e.g., purchasing department manager). Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role. This button displays the currently selected search type. Survey #150, Paud Road,
Accounts Receivable Analyst, Cash Analyst, Provides view-only reporting access to specific areas. In SAP, typically the functions relevant for SoD are defined as transactions, which can be services, web pages, screens, or other types of interfaces, depending on the application used to carry out the transaction. 1. 22 ANSI-INCITS, ANSI/INCITS 359-2004, Information TechnologyRole-Based Access Control, American National Standards Institute (ANSI) and InterNational Committee for Information Technology Standards (INCITS), 2004 5 Ibid. We will look into the wording in the SSP to clear up the confusion. Harnessing Oracle Governance Risk and Compliance. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. Roles may be generic (e.g., requester) or specific (e.g., purchasing department manager). Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role. This button displays the currently selected search type. Survey #150, Paud Road, Workday security groups follow a specific naming convention across modules. The term Segregation of Duties (SoD) refers to a control used to reduce fraudulent activities and errors in financial reporting. ISACA is, and will continue to be, ready to serve you. ISACA, the global organization supporting professionals in the fields of governance, risk, and information security, recommends creating a more accurate visual description of enterprise processes. As such, when performing an SoD analysis, the users various security assignments should be considered.
Considering processes and [risk factors] outside of the system are just as important as those inside the system, if one wants to look at fraud risk holistically.17 For example, a manager may authorize payments for accounts receivable; the same manager might use the same data coming from accounts receivable to draft a report to be shared with the companys executives. These duties are said to be segregated. Making the Most of the More: How Application Managed Services Makes a Business Intelligence Platform More Effective, CISOs: Security Program Reassessment in a Dynamic World, Zero Trust Architecture: Removing the Buzz, Building a Successful Data Protection Program, Common Frameworks for Maturing Security Programs, Limited Spend, Maximum Protection: Adaptive Microsoft Business Solutions. Role engineering is a discipline in itself, aimed at defining a common set of roles that can be used to assign to users grants and privileges on applications in a consistent and repeatable way.22 Role-based access control (RBAC) follows some common models, as described by the American National Standards Institute (ANSI) standard 359-2004.23. Best Practice Tips for Segregation of Duties in Oracle E. Understand the difference Beyond certificates, ISACA also offers globally recognized CISA, CRISC, CISM, CGEIT and CSX-P certifications that affirm holders to be among the most qualified information systems and cybersecurity professionals in the world. Each role is responsible for the following: 1) Human resources This can be performed by the human resources department hiring new employees and maintaining records of the employees hire date and salary information. SoD matrices can help keep track of a large number of different transactional duties. Get an early start on your career journey as an ISACA student member. Get the SOD Matrix.xlsx you need. Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs. WebWorkday Chief Diversity Officer. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats. Such checking activity may be viewed as an authorization duty or a verification/control duty. Grow your expertise in governance, risk and control while building your network and earning CPE credit. Our certifications and certificates affirm enterprise team members expertise and build stakeholder confidence in your organization. While SoD may seem like a simple concept, it can be complex to properly implement. OR.
Process descriptions may be described at a closer level of detail in the enterprises. Assets as Scoping Boundaries Such entities may be single individuals or groups. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. 7 ISACA, COBIT 5: Enabling Processes, USA, 2012 WebWhether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable their management team to promote an effective, efficient, compliant and controlled execution of business processes. It is important thatregular comprehensive reviews are undertaken, asperforming spot checks on the configurationwillnot suffice. Mapping Activities With Duties The traditional form of segregation leaves all authorizations to an individual (e.g., the department manager) and custody or recording operations to a second individual.16. www ey com. Establish Standardized Naming Conventions | Enhance Delivered Concepts.
Webdemande lettre de recommandation universitaire; schneider funeral home obituaries janesville, wi; colorado high school enrollment numbers; mobile homes for rent in austin, tx by owner A second boundary may be created by the processes that transform the assets or their status. WebThe concept of Segregation of Duties is to separate the major responsibilities of authorizing transactions, custody of assets, recording of transactions and reconciliation/verification of transactions for each business process. Harnessing Oracle Governance Risk and Compliance. With time, conflicts can be unintentionally introduced, allowing controls to be circumvented if careful consideration is not given to each configuration change. To address such concerns, compensating controls can be introduced after thorough risk analysis10 to reduce the vulnerabilities in ineffectively segregated functions, which include the risk of errors, omissions, irregularities and deficiencies in process quality. The segregation of duties matrix should include the process or process steps and authorizations checked. I. Segregation of Duties Definition: Segregation of duties is a key internal control. Select Accept to consent or Reject to decline non-essential cookies for this use. It is used to ensure that errors or irregularities are prevented or detected on a timely basis by employees in the normal Handle the related asset. To do this, SoD ensures that there are at least two Best Practice Tips for Segregation of Duties in Oracle E. Workday at Yale HR Payroll Facutly Student Apps Security. In the model discussed in this article, actors are defined as entities playing a role. Get in the know about all things information systems and cybersecurity. For example, account manager, administrator, support engineer, and marketing manager are all business roles within the organizational structure. Because it reduces the number of activities, this approach allows you to more effectively focus on potential SoD conflicts when working with process owners. 3. ChatGPT, the Rise of Generative AI and Whats Next, No, Post-Quantum Cryptography Finalist CRYSTALS-Kyber Wasnt Hacked. Participate in ISACA chapter and online groups to gain new insight and expand your professional influence. Fill the empty areas; concerned parties names, places of residence and phone Ensure that attention is given to who can perform tasks as unlike business processes, tasks do not contain Approvals or Review steps. A visual depiction of processes can be used as the basis to build a matrix of activities, which are then checked for incompatibilities.19 Those who evaluate SoD on processes written at this high level of detail should consider doing the following: The first choice has the advantage in that it reduces the size of the matrices. This 'carve out' helps enforce your Segregation of Duties policy. Understanding and management of system integrations. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. However, this approach does not eliminate false positive conflictsthe appearance of an SoD conflict in the matrix, whereas the conflict is purely formal and does not create a real risk. In fact, checking SoD among all actors against all activities in a complex enterprise, aside from being impractical, would be meaningless. Webworkday segregation of duties matrix. ISACA membership offers these and many more ways to help you all career long. WebResponsible for HR audits such as SOX, Segregation of Duties, and Total Recertification audits; PROFESSIONAL EXPERIENCE. Your responsibilities include, but are not limited to fulfilling the following duties: Apply software engineering background in a core language, such as Java, C++, or C#, with the ability to participate in the design and implementation of applications, including: Webservices - multilayer service structuring for security The term user profile is used throughout technical literature with different meanings. Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert Reconcile the transaction. Record the transaction. There are no conflicts. For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. In many cases, segregation of duties is required by law or standards in areas such as accounting, corporate governance and information security. Within a given business cycle there could be task on task combinations or a mixture of tasks and business processes steps. Processes are separate, but they are related to an asset they have in common. He concentrates on the telecommunications and finance industries. 19 Op cit, Singleton Of course, SOX-friendly regulatory technology can help by proactively detecting and highlighting any Workday SoD conflicts to mitigate the risk of fraudulent activity or accidental wrongdoing. His areas of expertise include IT governance and compliance, information security, and service management. When proper SoD is applied, actors performing incompatible duties are different entities. Managing Conflicts In Workday for a complete Segregation of Duties policy, you will also need to look at Maintain Assignable Roles and ensure that security assignments are restricted. To avoid this pitfall, ensure that a Subject Matter Expert (SME) reviews the rulesets and ranks each risk, careful consideration should be given to each check and the associated business risk identified. First, we must look to see who can perform the task Maintain Payment Elections (This task is used to update the bank details to where a worker will be paid) and secondly, we must look to see who can perform a compensation business process, Request Compensation Change, for instance. We are all of you! You may decide to use a combination of the supplied policy and your own configured modifications. An effective SoD mitigates all risk deriving from the risk scenarios presented in figure 2. Kothrud, Pune 411038, What CXOs Need To Know: Economic Recovery Is Not An End To Disruption, Pathlock Named to Inc. 5000 List After Notable Expansion, Helping the worlds largest enterprises and organizations secure their data from the inside out, Partnering with success with the world's leading solution providers, Streamlining SOX Compliance and 404 Audits with Continuous Controls Monitoring (CCM). Requiring segregation to be applied between individuals or between collective entities gives rise to the following different levels of segregation, depending on the organizational constraints that are required for SoD to be recognized as such: Incompatibilities Available 24/7 through white papers, publications, blog posts, podcasts, webinars, virtual summits, training and educational forums and more, ISACA resources. Given the potential for fraud and impact of human oversight / error,it is sensible to seek some form of automated analysis that reviews the entire tenant populationas often as possible. Design, perform and complete Internal Controls walkthrough and testing to ensure adequate level of internal controls within the areas of general ledger, revenue, accounts payable, payroll, HR, IT etc. The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. Generally, have access to enter/ initiate transactions that will be routed for approval by other users. ISACA delivers expert-designed in-person training on-site through hands-on, Training Week courses across North America, through workshops and sessions at conferences around the globe, and online. Provides administrative setup to one or more areas. ISACA is fully tooled and ready to raise your personal or enterprise knowledge and skills base. +1 469.906.2100 As Kurt Lewin said, Theres nothing more practical than a good theory.26, 1 Singleton, T.; What Every IT Auditor Should Know About Proper Segregation of Incompatible IT Activities, ISACA Journal, vol. The second process carries some risk related to SoD due to conflicting activities on the same asset. Websegregation of payroll duties with the aim of minimizing errors and preventing fraud involving the processing and distribution of payroll. While it is fair to say the lions share of your SoD conflicts will come from transactions that are controlled by one or more business processes, this is not the only thing you have to consider. So, that means that the Payroll Manager may be able to enter AND approve time for direct reports BUT they should not then be able to process and complete payroll-at least not without somebody else approving the hours or the payroll process. Segregation of duties is increasingly relevant to internal control regulations. Exceptional experience in Workday's Core HR (HCM), Benefits, Compensation (Basic and Advanced), Talent and Performance Management, Absence, ESS/MSS, Recruiting, Time Tracking. 6, 2012 workday segregation of duties matrix. 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing,
LinkedIn and 3rd parties use essential and non-essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads (including professional and job ads) on and off LinkedIn. Another mitigating control Workday provides within the business process definition is Advanced Routing Restrictions which again will help to hugely reduce the amount of data included for analysis. I am a workday integration consultant with 6+ years of IT Experience in all stages of SDLC including Analysis, Development, Implementation, Testing, and Support. WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. 2 Ghosn, A.; Segregation of Duties, American Institute of Certified Public Accountants, 2014, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/Auditing/InternalControl/Pages/value-strategy-through-segregation-of-duties.aspx In some cases, conflicting activities remained, but the conflict was on only a purely formal level. 6: Find the Right Tools to Help. 12 Op cit, Hare Still, SoD governance may benefit from introducing further controls to reduce risk to acceptable levels. Whether you are in or looking to land an entry-level position, an experienced IT practitioner or manager, or at the top of your field, ISACA offers the credentials to prove you have what it takes to excel in your current and future roles. SAP SOD Segregation of Duties STechies. The traditional approach to SoD mandates separation between individuals performing different duties. I hope this helps but feel free to follow up. 5, 2009 Workday HRIS Analyst/Team Lead. Processes must be thoroughly analyzed and some choices have to be made to detect and resolve potential conflicts. There are various other nuances and considerations that should not be missed when reviewing existing segregation of duty controls, such as business process delegations and correct permissions. SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment. Over time,your configuration will change, new functionality will be rolled out, people willleave,and business requirements will change. While reducing the time it takes to manually audit SoD requirements, regulatory technologies like Smart Audit also streamline the SOX compliance process and offer organisations the comfort of an always-on approach to security monitoring. This layout can help you easily find an overlap of duties that might create risks. SoD is a control and, as such, should be viewed within the frame of risk management activities. Preliminary activities requiring verifications from every actor involved are the very reason to invoke SoD: They provide a consistent set of checks and balances that ensures that operations abide by rules and procedures. 4, 2014 WebOur handbook covers how to audit segregation of duties controls in popular enterprise applications using a top-down risk-based approach for testing Segregation of Duties controls in widely used ERP systems: 1. Copyright 2023 Kainos. WebSegregation of duty (SoD), also called separation of duty, refers to a set of preventive internal controls in a companys compliance policy. Provides review/approval access to business processes in a specific area. shipment arrive at us cross border sub contractor a workday segregation of duties matrix. In addition, some of our leaders sit on Workdays Auditor Advisory Council (AAC) to provide feedback and counsel on the applications controlsfunctionality, roadmap and audit training requirements. SOD, a long-standing building block of sustainable risk management and internal controls, is a checks-and-balances approach that prevents a single person from controlling all aspects of a transaction. Encyclopaedia Britannica, www.britannica.com/biography/kurt-lewin. Open it using the online editor and start adjusting. All rights reserved. Please see www.pwc.com/structure for further details.